Nmap 7.10 Security released, Available for Ubuntu and Linux Mint (Ubuntu Derivative System)
Nmap 7.10 is released, you can install on Ubuntu 16.04 Xenial Xerus, Ubuntu 15.10 wily werewolf, Ubuntu 15.04 vivid Vervet, ubuntu 14.10 Utopic Unicorn, Ubuntu 14.04 Trusty Tahr (LTS), Linux Mint 17.1, Linux Mint 17.2, Linux Mint 17.3 and other Ubuntu derivative systems
Nmap is an open source and cross-platform software that provides users with one of the most powerful network discovery and security auditing utility appreciated by numerous system administrators and security professionals around the world.
Features at a glance
Key features include the ability to monitor service and host uptime, manage service upgrade schedules, do network inventory, discover available hosts on a network based on raw IP packets, as well as to discover running services and operating systems on a specific network.
In addition, it supports a wide range of advanced network mapping techniques, including ping sweeps, TCP/UDP port scanning mechanisms, as well as the ability to scan networks of hundreds of thousands of computers.
What New in version 7.10 :
[NSE] Added 12 NSE scripts from 7 authors, bringing the total up to 527! They are all listed at https://nmap.org/nsedoc/, and the summaries are below (authors are listed in brackets):
- [GH#322] http-apache-server-status parses the server status page of Apache’s mod_status. [Eric Gershman]
- http-vuln-cve2013-6786 detects a XSS and URL redirection vulnerability in Allegro RomPager web server. Also added a fingerprint for detecting CVE-2014-4019 to http-fingerprints.lua. [Vlatko Kosturjak]
- [GH#226] http-vuln-cve2014-3704 detects and exploits the “Drupalgeddon” pre-auth SQL Injection vulnerability in Drupal. [Mariusz Ziulek]
- imap-ntlm-info extracts hostname and sometimes OS version from NTLM-auth-enabled IMAP services. [Justin Cacak]
- ipv6-multicast-mld-list discovers IPv6 multicast listeners with MLD probes. The discovery is the same as targets-ipv6-multicast-mld, but the subscribed addresses are decoded and listed. [Alexandru Geana, Daniel Miller]
- ms-sql-ntlm-info extracts OS version and sometimes hostname from MS SQL Server instances via the NTLM challenge message. [Justin Cacak]
- nntp-ntlm-info extracts hostname and sometimes OS version from NTLM-auth-enabled NNTP services. [Justin Cacak]
- pop3-ntlm-info extracts hostname and sometimes OS version from NTLM-auth-enabled POP3 services. [Justin Cacak]
- rusers retrieves information about logged-on users from the rusersd RPC service. [Daniel Miller]
- [GH#333] shodan-api queries the Shodan API (https://www.shodan.io) and retrieves open port and service info from their Internet-wide scan data. [Glenn Wilkinson]
- smtp-ntlm-info extracts hostname and sometimes OS version from NTLM-auth-enabled SMTP and submission services. [Justin Cacak]
- telnet-ntlm-info extracts hostname and sometimes OS version from NTLM-auth-enabled Telnet services. [Justin Cacak]
- Integrated all of your IPv4 OS fingerprint submissions from October to January (536 of them). Added 104 fingerprints, bringing the new total to 5089. Additions include Linux 4.2, more Windows 10, IBM i 7, and more. Highlights: http://seclists.org/nmap-dev/2016/q1/270 [Daniel Miller]
- Integrated all of your service/version detection fingerprints submitted from October to January (508 of them). The signature count went up 2.2% to 10532. We now detect 1108 protocols, from icy, finger, and rtsp to ipfs, basestation, and minecraft-pe. Highlights: http://seclists.org/nmap-dev/2016/q1/271 [Daniel Miller]
- Integrated all 12 of your IPv6 OS fingerprint submissions from October to January. The classifier added 3 new groups, including new and expanded groups for OS X, bringing the new total to 96. Highlights: http://seclists.org/nmap-dev/2016/q1/273 [Daniel Miller]
- [NSE] Upgrade to http-form-brute allowing correct handling of token-based CSRF protections and cookies. Also, a simple database of common login forms supports Django, WordPress, MediaWiki, Joomla, and others. [Daniel Miller]
- [Zenmap] [GH#247] Remember window geometry (position and size) from the previous time Zenmap was run. [isjing]
- New service probe for CORBA GIOP (General Inter-ORB Protocol) detection should elicit a not-found exception from GIOP services that do not respond to non-GIOP probes. [Quentin Hardy]
- [GH#284] Fix retrieval of route netmasks on FreeBSD. IPv6 routes were given /32 netmasks regardless of actual netmask configured, resulting in failed routing. Reported by Martin Gysi. [Daniel Miller]
- [GH#272][GH#269] Give option parsing errors after the usage statement, or avoid printing the usage statement in some cases. The options summary has grown quite large, requiring users to scroll to the top to see the error message. [Abhishek Singh]
- [GH#249][Nsock] Avoid a crash on Windows reported by users using Zenmap’s Slow Comprehensive Scan profile. In the case of unknown OpenSSL errors, ERR_reason_error_string would return NULL, which could not be printed with the “%s” format string. Reported by Dan Baxter. [Gisle Vanem, Daniel Miller]
- [GH#293][Zenmap] Fix a regression in our build that caused copy-and-paste to not work in Zenmap on Windows.
- Changed Nmap’s idea of reserved and private IP addresses to include 169.254/16 (RFC3927) and remove 6/8, 7/8, and 55/8 networks. This list, in libnetutil’s isipprivate function, is used to filter -iR randomly generated targets. The newly-valid address ranges belong to the U.S. Department of Defense, so users wanting to avoid those ranges should use their own exclusion lists with –exclude or –exclude-file. [Bill Parker, Daniel Miller]
- Allow the -4 option for Nmap to indicate IPv4 address family. This is the default, and using the option doesn’t change anything, but does make it more explicit which address family you want to scan. Using -4 with -6 is an error. [Daniel Miller]
- [GH#265] When provided a verbosity of 0 (-v0), Nmap will not output any text to the screen. This happens at the time of argument parsing, so the usual meaning of “verbosity 0” is preserved. [isjing]
- [NSE][GH#314] Fix naming of SSL2_RC2_128_CBC_WITH_MD5 and SSL2_RC2_128_CBC_EXPORT40_WITH_MD5 ciphers in sslv2 in order to match the draft specification from Mozilla. [Bertrand Bonnefoy-Claudet]
- [NSE][GH#320] Add STARTTLS support to sslv2 to enable SSLv2 detection against services that are not TLS encrypted by default but that support post connection upgrade. This will enable more comprehensive detection of SSLv2 and DROWN (CVE-2016-0800) attack oracles. [Tom Sellers]
- [NSE][GH#301] Added default credential checks for RICOH Web Image Monitor and BeEF to http-default-accounts. [nnposter]
- Properly display Next-hop MTU value from ICMP Type 3 Code 4 Fragmentation Required messages when tracing packets or in Nping output. Improper offset meant we were printing the total IP length. [Sławomir Demeszko]
- [NSE] Added support for DHCP options “TFTP server name” and “Bootfile name” to dhcp.lua and enabled checking for options with a code above 61 by default. [Mike Rykowski]
- [NSE] whois-ip: Don’t request a remote IANA assignments data file when the local filesystem will not permit the file to cached in a local file. [jah]
- [NSE] Updated http-php-version hash database to cover all versions from PHP 4.1.0 to PHP 5.4.45. Based on scans of a few thousand PHP web servers pulled from Shodan API (https://www.shodan.io/) [Daniel Miller]
- Use the same ScanProgressMeter for FTP bounce scan (-b) as for the other scan types, allowing periodic status updates with –stats-every or keypress events. [Daniel Miller]
- [GH#274] Use a shorter pcap_select timeout on OpenBSD, just as we do for OS X, old FreeBSD, and Solaris, which use BPF for packet capture and do not have properly select-able fds. Fix by OpenBSD port maintainer [David Carlier]
- Print service info in grepable output for ports which are not listed in nmap-services when a service tunnel (SSL) is detected. Previously, the service info (“ssl|unknown”) was not printed unless the service inside the tunnel was positively identified. http://seclists.org/nmap-dev/2015/q4/260 [Daniel Miller]
- [NSE] [GH#242] Fix multiple false-positive sources in http-backup-agent. [Tom Sellers]
How to Install Nmap 7.10 on Ubuntu and Linux Mint (Ubuntu Derivative System) :
To install and update Nmap 7.10 on Ubuntu 16.04 Xenial Xerus, Ubuntu 15.10 wily werewolf, Ubuntu 15.04 vivid Vervet, ubuntu 14.10 Utopic Unicorn, Ubuntu 14.04 Trusty Tahr (LTS), Linux Mint 17.1, Linux Mint 17.2, Linux Mint 17.3 and other Ubuntu derivative systems, open a new Terminal window and bash (get it?) in the following commands:
Download :
wget https://nmap.org/dist/nmap-7.10.tar.bz2
Extract Tarball :
bzip2 -cd nmap-7.10.tar.bz2 | tar xvf –
Move to folder nmap :
cd nmap-7.10
Configure and Install :
./configure
make
sudo su
make install
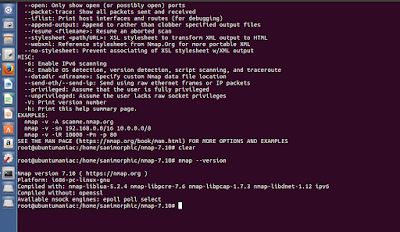
after you installed nmap, check your nmap version. open terminal and follow the command :
sudo su
nmap –version
Like a Picture :
Enjoy! I hope this article adding you more clarity.
Nmap 7.10 Security released, Available for Ubuntu and Linux Mint (Ubuntu Derivative System)
 Reviewed by Ubuntu Maniac
on
3:33:00 AM
Rating:
Reviewed by Ubuntu Maniac
on
3:33:00 AM
Rating:
 Reviewed by Ubuntu Maniac
on
3:33:00 AM
Rating:
Reviewed by Ubuntu Maniac
on
3:33:00 AM
Rating:




No comments: